After the unprecedented year we’ve just experienced, the last thing you need is to have your accounting data compromised or stolen. It would be impossible to reconstruct your QuickBooks file from scratch, and you can’t afford to have a hacker steal any of your funds.
There are multiple steps you can take to protect yourself from threats, both internal and external. QuickBooks itself offers some safeguards. Strong company policies can also help safeguard against data theft or destruction. And some of your security guidelines should just come from using common sense.
Here’s a look at what you can do.
Keep your systems safe
There are countless ways you can protect your data by maintaining the integrity of the computer that’s running QuickBooks. Some involve the same steps you would take to safeguard all the applications and information you have stored there. You should have reputable antivirus/anti-malware software installed. Use strong passwords. Keep up with system updates.
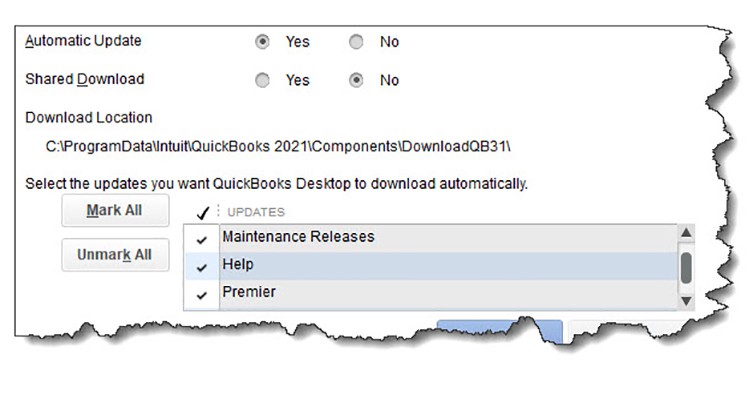
Updates and backup
QuickBooks’ own updates are critical, too. You can start these manually, but we recommend setting up automatic updates. Open the Help menu and click on Update QuickBooks Desktop. Click the Options tab to access this tool.
Frequent, safely stored backups are another essential element of overall data security. If your system is compromised by an intruder, you’ll need to be able to restore your most recent QuickBooks file when it’s safe again. Go to File | Back Up Company to set up either a local or an online backup. Use one of these tools at the end of any day you’ve entered anything on QuickBooks. We can help you with backup if you’re not sure how to do it.
Networks and smartphones
If you have multiple PCs that run on a network, it’s important to maintain that system’s health, too, since an intrusion at one workstation can affect everyone. You can do this by:
- Discouraging employees from browsing the web excessively and downloading unnecessary software.
- Encouraging responsible handling of emails (no clicking on unknown attachments, no personal email on work computers, etc.)
- Installing network monitoring software or hiring a managed IT service that only charges when you need them.
Do your employees have company-issued smartphones? Make sure their security systems are sound. Set policies to protect them. For example, tell employees they should never use them on a public wi-fi network or install personal apps on them.
Internal fraud possible
No business owners anticipate that their own employees would steal from them. But it happens, and it can do tremendous financial damage. Minimize your chances of being victimized by limiting the access that employees have to sensitive information.
Go to Company | Set Up Users and Passwords, then click Set Up Users. You should be listed there as the Admin. Click Add User and supply a username and password. If you’re not sure how many users are supported on your license or need to add more, contact us. Click Next and then click the button in front of Selected areas of QuickBooks. Click Next again. On the next several screens, you’ll designate that user’s access in areas including Purchases and Accounts Payable and Checking and Credit Cards. When you come to the end of the wizard, click Finish.
You might consider running a background check when you hire someone who will have access to QuickBooks. It’s become a more common business practice.
QuickBooks provides additional tools that can be helpful in tracking down suspicious activity. You can view the Audit Trail, for one. Go to Reports | Accountant & Taxes | Audit Trail. This report displays a comprehensive list of transactions that have been entered and/or modified.
There are other reports that may be helpful, like Missing Checks, Voided/Deleted Transactions, and Purchases By Vendor.
A never-ending process
It’s so easy to get caught up in the daily work of running your business that you forget to take the steps required to keep your QuickBooks data — and all your computer hardware and software — safe. We get that.
Further, you might think that you’re an unlikely target because you’re a small business. Hackers count on you thinking that, though the reality is that you don’t have to be a big corporation to be the victim of cybercrime. Whether or not criminals get access to your funds, they can do a lot of damage that will end up costing you more time and money than you might think.
It’s important to stay vigilant. Security should be considered whenever you deal with financial transactions – especially where the internet is involved. If we can be of assistance as you set up safeguards and company policies, let us know. As always, reach out to KraftCPAs for answers to any questions you might have about QuickBooks operations.
© 2021