Businesses and nonprofit organizations continue to adapt to new lease accounting standard rules, the result of several years of federal planning and adjustments.
Accounting Standards Codification 842 (ASC 842) now applies to private companies and nonprofit organizations with fiscal years beginning after December 15, 2021, and it significantly changes the accounting for leases.
Still not sure how ASCS 842 will affect you or your balance sheet? Let’s start at the beginning.
Allocate resources
To implement the new standard, first decide who on your team will be responsible for implementing it. That person should review all current leases and review and, going forward, approve all new leases that are applicable to ASC 842. A program such as Microsoft Excel can help with some of the math and calculations, or look into any of the specialized lease software currently available.
Definition of a lease
ASC 842 defines a lease as a contract “that conveys the right to control the use of an identified asset… for a period of time in exchange for consideration.”
When reviewing any lease contract, look for these three elements:
- A clearly identified asset.
- Specified rights to control the identified asset. Consider options to extend the lease, cancel the leases, and the likelihood that those options are exercised.
- Hidden servicing contracts. Look closely for leases or contracts embedded in those agreements that also could be subject to ASC 842.
Under ASC 842, a lessee can choose a short-term lease accounting policy that’s less than 12 months and doesn’t have an option to purchase the chosen asset. A short-term lease accounting policy will recognize the lease payment over the lease term on a straight-line basis and, as a result, right-of-use assets and lease liabilities would not be recorded for short-term leases.
Lease classification
ASC 842 retains the two-model approach of classifying leases as operating or finance leases (formerly capital leases). Regardless of the classification type, most leases will be recorded on the balance sheet as a right-to-use asset or liability.
If one or more of the following criteria are met at the start of the lease, the lease would be considered a finance lease:
- The lease transfers ownership of the underlying asset to the lessee by the end of the lease term.
- The lease grants the lessee an option to purchase the underlying asset, and the lessee is reasonably certain to exercise the option to purchase.
- The lease term is for a major part of the remaining economic life of the underlying asset.
- The present value of the sum of the lease payments and any residual value guaranteed by the lessee equals or exceeds substantially all of the fair value of the underlying assets.
- The underlying asset is of such a specialized nature that it’s expected to have no alternative use to the lessor at the end of the lease term.
If none of these lease classification criteria are met, the lease is classified as an operating lease.
Discount rate
To determine the current value of the sum of the lease payments, apply a discount rate. Three discount rate options are provided under ASC 842:
- Rate implicit in the lease. The rate implicit in the lease should be used if readily determinable.
- Incremental borrowing rate. When the rate implicit in the lease is not readily determined, the incremental borrowing rate will appl. The incremental borrowing rate is the lessee’s rate for a hypothetical, collateralized loan with similar terms as the lease.
- Risk-free rate. Nonprofit entities may elect an accounting policy to use the risk-free rate for a period similar to the lease term. The risk-free rate is the rate of a zero-coupon U.S. Treasury instrument.
How to account for the leases
The initial accounting for the leases is the same whether it’s a finance or operating lease.
On the start date of the lease, the lessee records a lease liability for the present value of the sum of the lease payments and a right-of-use asset equal to the lease liability. The subsequent accounting for the lease costs and amortization of the right-of-use assets varies depending on the classification as a finance or operating lease.
For a finance lease, the asset is amortized straight-line over the lease term or the useful life of the underlying asset. Interest costs are recognized for the accretion of the lease liability and recognized as interest expense.
An operating lease is recorded as a lease or rent expense and is recognized on a straight-line basis over the lease term.
Implementation options
ASC 842 went into effect for calendar years beginning with the December 31, 2022, year-end financial statements. There are two options for initial implementation:
The effective date method. Using this option, the lessee will implement the standard effective January 1, 2022, and not restate the 2021 or prior comparative financial statements. The accounting standard change is made through a cumulative-effect adjustment recognized as of the effective date.
The comparative method. With this method, all periods presented will fall under ASC 842 guidelines. The accounting standards change is made through a cumulative-effect adjustment recognized as the beginning of the earliest period presented.
Changes to your financial statements
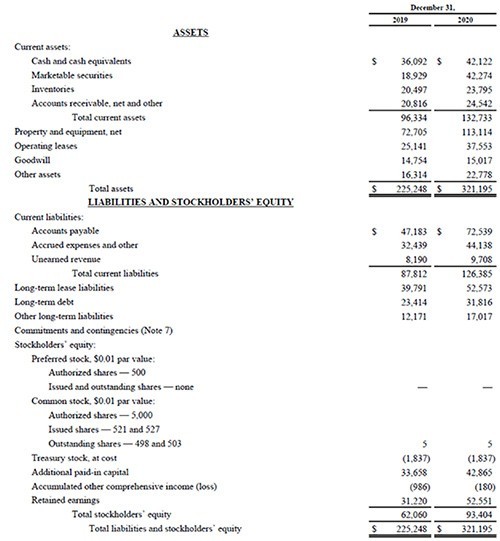
Balance sheet. Right-of-use assets and lease liabilities should be presented as a separate line item on the balance sheet or disclosed separately in the notes to the financial statements. If they aren’t presented separately on the balance sheet, the note must indicate which line items on the balance sheet include the right-of-use assets and lease liabilities.
An example of the balance sheet changes:
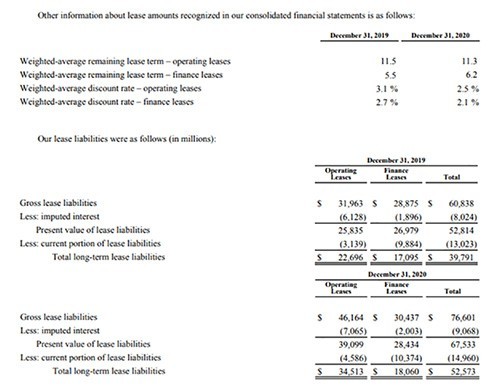
Footnotes to the financial statements. Expanded disclosures required for both lease classifications include:
- Description of leases.
- Terms and conditions, including purchase options and termination penalties.
- Judgment and assumptions made, including capitalization thresholds.
- Amortization of right-of-use assets, interest costs, and periodic lease expense associated with leases.
- Discount rate(s) (weighted average).
- Remaining lease terms (weighted average).
Application of the standard will not result in any adjustment to equity for treatment of either type of lease.
This is an example of the footnote disclosures:

ASC 842 has been debated and adjusted quite a bit over the past several years before finally going into effect, so the end result can be confusing and tedious. Contact us or any of the professionals on our assurance services team if you have questions about how ASC 842 applies to you.
© 2022 Kraft CPAs PLLC